ip checker fun..
Or.. "How my IP checker revealed gaping security holes all over the web as well as some highly dubious ISP practices.."My external ip checker script..
https://corz.org/ip
..is pretty handy. Whenever you need your external IP Address, there it is. And in plain text, so you can insert it into scripts, whatever you like. I've had it running for years, providing a free service to anyone who needs it.
On a hunch (looking for some missing bandwidth), I decided to add a basic logging capability, suspecting that some were using it more than others. It's such a simple script that it doesn't call the usual site initialization or any such thing, simply spits out your IP, so misses out on the usual site logging. Just as well..
Sure, I suspected that it was getting used a fair bit but really, I had NO IDEA! In the first minute of logging, it racked up over 2000 hits. That's right, TWO THOUSAND PER MINUTE! Holy Sheeite! On the plus side, I can now tell folk that I have a page on site that gets three million hits a day!

I left it logging overnight while I slept and six hours later I checked again - almost 100MB of log. Oh man! Also, I suspect the hits are simply coming in so fast that the logger doesn't have enough time to lock/write/unlock the log file quickly enough to catch them all! Crazy!
The first thing I've done is to enable some simple throttling to the ip checker. You can now check no more than once every minute. The first time you attempt to check your IP within this time, you get a message to this effect. Thereafter nada, until you back off for a minute and try again.
That's the technical bit out of the way, now for the fun..
So I have a list of a zillion IP addresses and noticed that about half a zillion of them are from the same IP block, one "VNPT", aka. "VIETNAM POSTS AND TELECOMMUNICATIONS". Interesting. It looks very like they have plugged the URL of my IP checker into their firmware somewhere! To be called every 13 seconds!
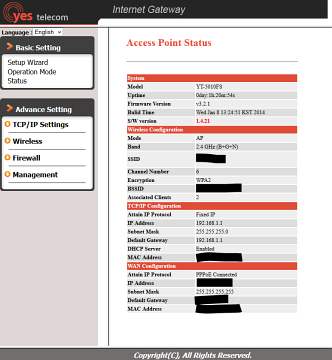
So I picked one of the IP addresses at random and popped it into my browser. Auth login prompt. Hmmm.
I enter admin/admin as the user/pass, wait a moment, and Voila!
I got root!
And here I am, browsing their router admin interface and laughing, shaking my head. Of course, I'm no stranger to this sort of malarkey. Before I started the whole BT Voyager section oh so many years ago, this sort of thing was commonplace. I've seen hundreds of router admin pages but, being a generally straight-up guy, haven't done anything nefarious whilst browsing around their personal settings (back in the day I would rename their WiFi SSID to "ChangeYourGatewayPassword" or some such fun. Slightly irritating for them, but a lot better than the alternative. I have no intention of attempting this with thousands of VNPT routers!).
So I pick another IP at random. Same story. And another. The same. And again. I do this twelve times and EVERY SINGLE IP IS WIDE OPEN! Not only with the WAN interface showing (yes, ISP's should never supply modems with this enabled), but still using the default admin/admin user/pass combination. This is not good.
It looks like VNPT is using old Yes Telecom hardware (Realtek/Zyxel routers), probably shipped with minimal instructions. Ultimately, as ISP's will tell you, the end-user is responsible for ensuring the security of their gateway device. But in order to do this, the average user (not power-user/techie/IT nerd) needs to be informed that it is insecure in the first place (which was the main rational behind the old BT Voyager section). Clearly this ISP like to keep its users in the dark. Perhaps they like the ability to login themselves and change stuff if "required".
I tried some other IPs, too; not VNPT. Six in total, five cameras (two quite private!) and another router (which had no security enabled AT ALL - courtesy of Tata Indicom). And do you know what, EVERY SINGLE DEVICE was setup to use the default username/password combination (except the router, which didn't even ask!). If I were some dubious individual looking to spy on folk, or mess with their life, I could have a field day! Instead, I try to blog some sense into the populace!
What is wrong with these people? I'd wager they don't leave their front door wide open when they go to work. Yet somehow their internet front door is allowed to stay open at all times. It makes no logical sense to set a super-duper 15 character WPA2 WiFi password in an attempt to thwart WiFi sniffers when someone can simply login to your gateway admin page and read it! I mean, come on!

So there you have it. Setup an external IP checker facility, get people using it, and Wham! You've got unlimited root access to thousands of gateway routers, cameras, and other interesting internet-enabled devices. Kinda scary.
for now..
;o)
ps. Your router doesn't have its WAN interface enabled, does it?
pps. Your router/IP camera/whatever wouldn't be using the default user/pass combination, would it?