
Hacking at the BT Voyager 205 adsl router modem
This started as a wee collection of miscellaneous telnet cli commands, tweaks, hacks and other fun for the BT Voyager 205 router. a.k.a. "Globespan Viking" (Globespan is now owned by conexant), but my original BT Voyager 205 text file started getting a lot of google-type action, so I eventually got around to doing a web page proper, as promised.What we now have is pretty much Viking Central, and owners of all the viking chipset based routers; BT Voyager 205, of course, CastleNet AR502, Dynalink RTA100, RTA500-D51, GlobespanVirata, Netgear DM602, Solwise SAR100 & SAR130, Riger db102, Callisto 821, BT Voyager 205, CastleNet AR502, Cell pipe 22A (21A) -BX-AR, Dynalink RTA100 (Viking I), Dynalink RTA500-D51 (Viking II), Siemens E-010-I, Speed Modem 50, Speed Modem 100, Tenda TED8620R and probably many others; as well as folks with no pretence of owning anything even remotely similar, drop by with their router woes and triumphs. It's been a lot of fun. Check out the full story in the many hundreds (make that thousands! -ed) of comments.
I'm told the voyager pages are a good read for other network n00bs, too, so if you're looking to find out what a "Static IP" is, or learn a few proxy tricks, setup a webserver, or maybe just soak up some network basics, you may just find what you need right here. I'll let you be the judge.
As well as how to configure the voyager router, most folks seem to be looking for security and stealth, NAT rules (with examples), port-forwarding, and porn, well, apart from the porn, it's all here!
There's been some re-organising, splitting up the data into separate pages (please see the menu at the top), usually in response to the groovy comments at the foot, clarifying and expanding things as we go along, mainly so people don't have to keep asking the same questions over and again.
Fire away! but do bear in mind, if it's a technical issue that's already been covered here, the response is unlikely to be what you'd hoped for! At least run through the troubleshooting checklist before asking FAQs. Otherwise, feel free to add a comment, or just rant and flame. There's no such thing as a stupid question, though barney's come pretty close (hehe, just kiddin' dude! ;o)
meet the black box...
Model : Viking Name : voyager Domain Name : corz.ath.cx Description : DSL Modem Location : Aberdeen, Scotland Contact : cor.. https://corz.org Vendor : GlobespanVirata Inc.,100 Schulz Drive, Red Bank,NJ 07701,U.S.A LogThreshold: 1 Object-id : 1.3.6.1.4.1.50000 HwVersion : 810020 SwVersion : V1.1 DSL Version : Y1921a System Time : Sat Nov 27 14:11:44 2004 Time Zone : GMT DST : On Services : physical datalink internet end-to-end applications UpTime(HH:MM:SS) : 13:37:23 Backup Interval : Disable Power Required : 16V ~ 1A [16VA] AC
It's worth investing a little time in getting to know the unit, setting it up properly. With only a couple of simple commands you can create a hardware-firewalled, safe, internet-enabled LAN environment for your home or organisation. The box comes free with BT's current 1MB/2MB broadband package, possibly other packages. With free adsl connexion thrown in, it's actually not a bad deal. At least until the limits set in, circa May 2005. *sigh*
The BT Voyager 205 is a good wee box. As well as a simple USB modem (you won't need to remove that sticker, ever!), it's a "real" router, so you can just connect it to an ethernet switch and tada! your whole LAN has internet. No drivers required! I repeat: NO DRIVERS REQUIRED!!! The unit can act simultaneously as a router AND a modem, all by itself.
Using ethernet, the voyager works independently of any computer, so it doesn't matter if you're running OS X, BSD, Linux, Solaris, Classic Mac OS, Amiga OS, even Windows®; this box can act as your "always on" internet gateway. It's got NAT, a good IP filter firewall with stateful inspection (don't believe the rubbish they tell you elsewhere!), dhcp server, access control, comprehensive attack protection, automatic DUC, the works! It begs to be tweaked and hacked, and we've already discovered some useful undocumented functionality doing just that, as well as render at least one unit completely unusable!

NO USB past this point!
Before we go any further..If you insist on using USB to connect to the router, expect to a) have lots of trouble with your internet connexion, b) be ignored here when you ask perfectly reasonable questions, and c) spend a lot of time at the troubleshooting page, on your own! Simon says, "Get a NIC!", or words to that effect, which is a "Network Interface Card" and will cost around three bucks in any currency. We really did have a Simon that said that! Check the comments.
But Kev tells us that if you go into your Windows Device Manager (run "devmgmt.msc") and bring up the properties for your USB root hubs, and on the "Power Management" tab, UNcheck the box where it says "Allow the computer to turn off this device to save power", you may at least not have to suffer the thing cutting out every five minutes. This will keep you going until you get a switch!
Okay, NOW we can start..
Getting Started..
Ironically, the best way to begin hacking this thing, is to start with the web interface..http://192.168.1.1 (the preset default address, you can change this)
If you have a static IP on your puter, ensure you are in the same "subnet", in other words; 192.168.1.something (if your whole LAN uses static IP's and they are *not* on that subnet, you can change the IP of the router to match your LAN, though you will have to temporarily flip your computer's IP to 192.168.1.3 to alter the router's IP to 192.168.0.1 (or whatever), oh the pain! but you can also create "virtual" ethernet connexions, serving multiple subnets)
note: the 205, as supplied by BT comes insecure out of the box. I think BT imagined the ethernet port would be used only by XBox and PS2 gamers, or perhaps they wanted to drop in sometime. Anyway, the unit connects itself to your favourite ISP right at startup (remember this if you are trying to setup the 205 for different ISP, like Tiscali, or AOL (puleeze!) or whatever, you'll need to enter your login details before you connect the 205 to the phone line!) so first thing to set is..
set this to "High", which is better than it was, but not a lot. Apply, and Save your changes. (the oddly-placed red save button appears on all the advanced pages) now you can breathe a little while you get this thing properly secure and working the way you want it to. after enabling the basic security, setup any other stuff you understand, save again, then go to..
and click the 'Save Config' button, which will save the current configuration to your hard drive.
this exported file is no more than a list of cli commands for the voyager router. with this list of commands, you can recreate your router's current state at any time in the future. make a copy of that file, and start adding to it. Later you can upload it to the router via FTP, and use it as your default command set.
Let's Hack!
With our current configuration safely backed-up, we can start to really hack this thing.There are two schools of thought as to how best to approach this task. Some folk prefer GUI tools, and others prefer a command line. Each has advantages and disadvantages. The main disadvantage of the cute web interface gui is that only some of the pages are available, however we have overcome this and though I personally prefer to use the command line to configure my router, I have created a couple of tools allowing GUI fans to access the "hidden" pages of the web interface, where you can now get to most every setting you will ever need to tweak. It's certainly easier to view the results in the web interface, anyway.
Those page selector tools are right below this article, above the comments. Conveniently, you can also open them in a separate window, and if you save the resultant page to your hard drive, you can use these tools at home, even when you're offline. If you have a webserver with php running, source is also provided.
But it's from the command line that ALL the settings are available. The ability to drag & drop commands into a telnet session, not to mention its scriptability, makes the shell ideal for a job like this. There's something wholesome about plain text commands, a particular clarity. So let's open a telnet session..
telnet
Telnet is just a protocol, like FTP is. It allows you to run a command line on a remote machine (in this case, the router). All modern operating systems have a Telnet program built-in, usually called simply "telnet". Only via telnet can we access the router's raw command line, where commands can be typed directly into the router's brain.When I first dropped into the command line (from my mac) I was frustrated by the inability to delete characters, or move around with the arrow keys. One wee mistake, and BANG! you have to start again. I tried using Putty, and other tools on the peecee, but still the same effect, eventually I just accepted that it was "a router thing".
However, if you open a plain old telnet session from a plain old DOS box, at least on XP, you have a magic telnet session that allows all these things! BobR tells me it's because of the "Terminal Emulation" mode used, of course! XP defaults to the old DEC vt100 emulation, which works perfectly! Cheers Bob!
Scattered throughout this area of the site are clickable links (there's one coming right up) which will, in theory, open a telnet session on your machine. And if you are running windows, you'll likely get the same magic telnet session as me!
by default the router lives at 192.168.1.1 so go into your shell and do..
telnet 192.168.1.1 <-- click here to telnet into your router!
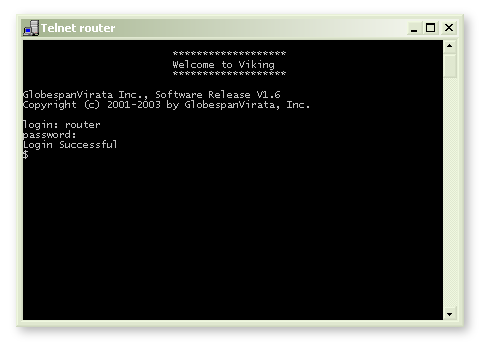
( note that inside my LAN "router" resolves to 192.168.1.1 )
The account login is the same as the web interface ( preset defaults are user: admin password: admin ) very secure! you can ftp in, too, but although there's lots to see, there's not a lot to do, at least, so far. we'll see. with the right firmware it might even do ssh.
On a mac, you can select any command line from this page (or your own script), drag it into your terminal (connected via telnet to the router, of course) and your hacks go live!
telnet tip: before you drag-and-drop, when you select the command, select the whole line, including the following line-break; then <enter> will be pressed for you as well. in bbedit, TextPad, EditPlus, etc., this can be achieved by simply clicking to the left of the line. (this also works in certain Linux desktop configurations) note: if you drag-and-drop from this page, make sure the example IP matches yours!
another tip: Ctrl-D will close most telnet/ssh sessions.
IMPORTANT: when you login to a telnet session, you will not see your password being entered, no asterixes, nothing, but for sure, it's going in just fine! Hit <enter> as normal, and you'll login without any problem. It's not broken, it's a security feature!
I've used greyed-out text here, to differentiate between the telnet commands and my comments, to (hopefully) make things clearer, at least, clearer than they were to me when I started messing with this thing this morning, getting most of my clues from Chinese web sites! they've had the Viking chipset a while, apparently. okay ...
In a telnet session with the router, you can type any command and then a space and then a ? to get help for that command, like this..
get ?which would produce a list of possible "get" commands, next you could do..
get ppp ? for a list of "get ppp" commands, etc.. this tip will save you hours!
for a list of "get ppp" commands, etc.. this tip will save you hours!?on it's own is the same as
helpwhich gets you a list of top-level commands.
use the UP key to recall the last input command. use this a lot!
after giving help, the cli puts that same command back on your current command line minus the "?", so you can build up long commands one command at a time, getting help all the way. neat. okay, first..
Stealth and Security..
You will probably want to begin by stealthing your router. A stealthed router sends a definite signal to any potential attacker, and also refuses to needlessly leak information about your computing environment. You can stealth a voyager 205 with just two simple commands..create ipf rule entry ruleid 5 dir out act accept storestate enable seclevel high medium low
create ipf rule entry ruleid 500000 ifname public dir in act deny seclevel high medium low
Much better! a simple start. Now you got stealth, nothing's getting in! so if you want to run any servers, ftp server, web server, whatever, or effectively use any p2p application, you'll need to create individual rules to allow this inbound traffic, inserting them numerically between the two magic stealth rules above. an example BitTorrent rule..
create ipf rule entry ruleid 6881 ifname public dir in act accept destport range 6881 6899 transprot eq tcp seclevel high medium lowAfter dropping in another rule for the±wire it looks something like this..
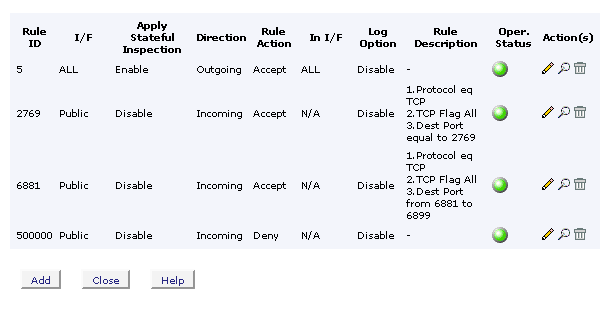
this screen is here ..
You might want to enable standard attack protections..
modify fwl global blistprotect enable attackprotect enable dosprotect enablethese should be on by default, do check your model/settings (and exported .cfg file).
who da bad boys? ..
get fwl blacklistto delete a firewall rule..
delete ipf rule entry ruleid 6881check out the stealth page for a great deal more information about stealthing your router, including important notes on firewall testing.
NAT (not an insect)
If there are a few or more users in your home/business/organisation, you'll likely want give them all internet access. broadband was made for sharing. this is where NAT comes in. NAT, or "Network Address Translation" is simply a way for multiple "private" computers to share a single "public" IP address.The NAT "gateway" (our beloved BT voyager 205) translates all the outbound requests from our individual "private" computers (called 192.168.1.whatever, safely inside our Local Area Network, or "LAN") and alters the packets so they appear to originate from a single "public" IP address (which is all the folk on the outside can see). When the requested packets return, the NAT reverses the translation, and routes the data back to the originating "private" machine. clever stuff.
Because the Voyager can apply "stateful inspection", inbound packets are examined on arrival, and only those packets we requested are forwarded on inside the LAN. Essentially nothing gets through the NAT unless we asked for it first, or, like the BitTorrent rule above, we specifically open up a port.
So first we.. NAT everything!
create nat rule entry ruleid 100000 naptI recently discovered that the voyager has a hidden NAT rule which does exactly this. Mine is rule ID no. 4294967295 ! I still add my own though, where I can see it.

port forwarding.. maximum 20 rules!
After opening ports to allow inward traffic, you need to route that traffic to a particular "private" computer inside your network. To do achieve this, we use port forwarding. It does exactly what is says on the can, forwarding the data packets on to the private machine.In order for this to work as expected, your private machines (machines at this side of the firewall) need to have "Static IP's". Most computers will, by default, get their IP address dynamically, that is, it will be assigned by the gateway computer, which is our router (aye, there's a wee computer inside there!). You'll need to ensure that dynamic IP addressing (dhcp) is disabled on your computer, and you have instead manually assigned a static IP to the computer, probably something like 192.168.1.3. For more information on how to do that, see here.
It could be argued that "my computer always gets assigned 192.168.1.3", but that's asking for trouble when, six months down the line, you add a laptop to the network and suddenly all your firewall rules stop working, and it takes you six hours of troubleshooting to figure out why! If you need DHCP, mindfully create a special pool of addresses, for "guests", or whatever. In a discipline with so many variables (networking) it makes a great deal of sense to convert as many as possible to constants. So with your target machine at a fixed, reliable, constant address; let's do it..
This example NAT rule will forward all inbound bittorrent traffic to a machine at IP address 192.168.1.3..
create nat rule entry ruleid 6881 rdr prot num 6 lcladdrfrom 192.168.1.3 lcladdrto 192.168.1.3 destportfrom num 6881 destportto num 6889Something very similar would work for any p2p application and protocol; eMule, edonkey, kazaa, LimeWire, WinMX, Gnutella, Direct Connect, etc, etc. same for servers; FTP server, Web Server, whatever.
check out the recipes page for lots more details and a whole bag of ready-made NAT rules!
As well as simple redirection, you can create different kinds, or "flavours" of NAT rule, and put ranges of ports into one rule, too. handy, because you can only have twenty rules maximum. you can also create IP ranges (aka round-robin), more useful for sharing load on multiple servers. check out the PDF's at the foot for an almost complete list of all the NAT, and many many other rules.
A simple NAT configuration might look like this..
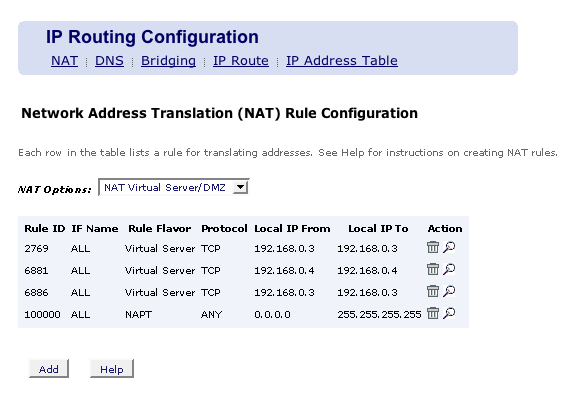
click the magnifying glass to look at stuff close up..
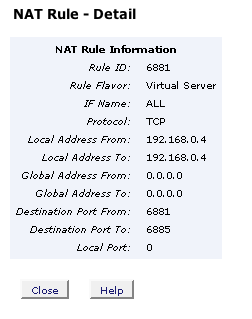
you'd think the "global address to" would need to be 255.255.255.255, but the voyager doesn't seem to care. I guess when neither are specified it just presumes you mean everything.
you can do..
create nat rule entry ?for a list of all the NAT options. You can delete a nat port forwarding rule like this..
delete nat rule entry ruleid 6881If you are looking for a particular solution, it's probably on the recipes page!
If not, consider making a donation, and request that it be added!
essential tweaks..
ppp link...
Enable ppp keepalive..modify ppp global keepalive enableppp sessions time-out after thirty minutes inactivity. let's change that..
modify ppp global pppsesstimer nevertimeout(for v1.8 firmware, replace "nevertimeout" with "99999")
time to live..
modify ip cfg ttl 64 network connexion limits...
The maximum number of IP sessions the modem can manipulate simultaneously is 512. the default is 192, let's fix that..modify nbsize maxipsess 512note: if you have upgraded to the v1.8 firmware (which I have not) you can only set that to 511, not 512.
for gamers..
Opening and closing lots of connexions quickly (like some p2p apps and most networked games do) can fill up that connexion table pretty fast, because you open new connexions before you have closed the old ones. exactly how long the old connexions stay open is up to you..modify nat global tcpidletimeout 3600 tcpclosewait 45 tcptimeout 30 udptimeout 90those are the default setting, but you can probably get off with using much lower values, especially if you search for game servers a lot, something like these..
modify nat global tcpidletimeout 1800 tcpclosewait 30 tcptimeout 10 udptimeout 15or even less. Every setup is slightly different; experimentation is the key to success. There are other parameters that may be set, too, for more details, open a telnet session with your router and do..
modify nat global ?replace a time server entry..
modify sntp cfg disable
delete sntp servaddr dname Time.apple.com
create sntp servaddr dname pool.ntp.org
modify sntp cfg enable
get sntp statsetc..
Get stats on stuff..get system
get nat stats
get ip stats
get sntp stats
get pfraw stats
get ethernet stats
get fwl stats
get dsl stats curr
get user
get ipf sessioncreate a new user..
create user name boss passwd mypassword root alg rules...
"Application Layer Gateways" are clever things, allowing you to run IRC and ICQ clients, FTP servers and the like without endless firewall hassles, thanks to the 205's "stateful inspection" mechanisms. Most of the common ones are already in place, but if you need something special, you can add it yourself.This example would allow you to connect successfully to an IRC server running on a non-standard port, in this case port 7000..
create alg port portno 7000 prot num 6 algtype mirc more than just for fun...
modify system contact "cor, https://corz.org"
modify system location "Aberdeen, Scotland"
modify system dname "corz.ath.cx"
modify system name "Starship Voyager 205"you can do them all at once, too..
modify system contact "cor, https://corz.org/" location "Aberdeen, Scotland" dname "corz.ath.cx" name "Starship Voyager 205"Would be fun to have a finger server on the unit, presenting this info to whoever asks. For more of these sorts of fun and games, don't forget to check out the tips & tricks page! (Hacks for Dynamic DNS, alternative DNS servers, ping, traceroute, custom logging and much more!)
cool it!
This box runs hot. There's enough anecdotal evidence going around to suggest that when things start to wonk out, heat can be a factor. In short, keep it somewhere cool, like under a window, or sit some nice flat-bottomed, metal object on top of it to act as a heat-sink, or both..If you REALLY want to cool it, check out this.
lastly..
Don't forget to check out the router directory in my public archive for many interesting files ( including PDF's containing ALL the possible commands), firmware utilities, patches, shell scripts, and much more..https://corz.org/public/docs/comms/router/
you can download the main two directly, here..
have fun!
;o) corz.org
ps.. the original protective sticker is still stuck over the USB socket of the Voyager 205,
and it's going to stay that way, too!
Useful Links..
click this link to go directly to your router
your router's built-in help system
collection of useful things
You go click, and the router goes, well, it just goes!
Goan save yourself four weeks of headaches!
don't even go there!
top class telnet client
weird solutions
and a great OS, to boot!
try the "Outils traduits" link
potentially useful (rta100+) software & firmware
useful free IP scanner, for finding lost routers
if you want to know what ports to open for what games


Before you ask a question..
PLEASE ensure you have at least run through the troubleshooter at the foot of the troubleshooting page and checked EVERYTHING!
Note: If your router isn't a Voyager 205, go here.
Please note: comments on this page are now disabled: but that doesn't mean I want you to mail me with your router troubles! If you want my time, the PayPal button is in the top-right of all pages!
NOTE: If you load this page with ALL comments, you will probably find someone has already asked your question, and been answered.
ive had some problems im not sure wheter its not my isp, when i play a game called css, i cant connect to server ive forwarded out ports.
i restart my router i can then connect but then i cant connect to anyother server untill i restart it.
my isp is tiscali im changeing isp who as there absolotly useless and they keep blameing my 205 for the problems....tards tbh they dont understand the concept that if i run it round a friends and they have tiscali it works fine and any other isp for that matter. i think im gunna change to bt......this site is great its helped me fine tune my router a treet
Hi, I am using Azureus and cannot get the green smiley. When I probe the port I have opening in the 205, mu router and my software firewall I just stealthed with GRC and probably stelathed on this site's probe. I can download torrents with a yellow smiley but not a green one. It seems to think I am still behind a firewall. Using WinXP SR2 with their firewall disabled. Also not running that silly service that XP Uses Using version 2.4.0.2 of Azureus. Anyone got any ideas. I have followed everything on these pages. Using a Linksys Router.
Thanks
Cor
Please! contact me m8
Regards Joker
Cor
Do you still live here??
i'm on linux and just so you know i'm getting the same problems on Linux - using KTorrent on kUbuntu
COR "Neospace, a fitting title for you. Because it's possible to create ranges with the 205, I have personally had no need to breach the 20 rule limit. Why not enter this new space, and discover for us? Slam in a heap of rules over telnet and see if the last ones still work."
If anyones interested, I dont seem to be having any troubles adding 25 rules, all seeem to be working fine. No problems to date. One just now with Azurres, but nothing that would jepordise my connection between my comp and router. (Hopes theres no underlying problem) But yeah, Seemingly, you can add as many as you like through telnet. Seems they nmust have put the limiter on it to stop normal people (Yes i mean normal People) from completely opening up there router to the rest of the world. Would seem like a good idea to me. But yeah, all in all. No problems so far. Ill keep you posted.
Take it easy peeps
Yeah, Joker! Still here! But I've been away for a few days, as often happens, especially in the Summer. I can't find your mail, but I haven't done a full scan yet; feel free to reply to that one I just sent you.
mub, afaik, there's no restriction on using high port numbers, I have servers running on a few high ports, and the 205 didn't mind at all. I used v1.6 firmware, though. But then, you port is *very* high. Scan the PDF for high ranges used for other things. By the way, in your situation, I'd ditch the 205, and use a simple modem.
grazazel, you'd be better off with a switch. Check the useful links section, above. If you can't afford the ten bucks, try enabling ICS on the main machine (follow the wizards).
Java, Bob, it just sound like you need to limit more. If you have 511 connexions to play with and Azzy is set to say, 500, that doesn't leave a lot of room for anything else. 300 max would be fine, say 200 max per torrent. Then run through your Azzy prefs, things like DHT may affect the total number of connexions. Those TCP/UDP timings can come down lots, too.
sam, you probably need to make some adjustments to your TCP/UDP (depending on the game) timings. Check out some of the ARSE game scripts (even if its not the game you play); they have lots of information and notes about this inside them.
dipper17, as well as creating the port-forwarding rule for the 205, did you forward the port in the linksys?
Neospace, interesting. I guess there must be a limit somewhere (the thing only has so much ram), so do let us know if you hit it!
for now..
;o)
like i said i've tried limiting connections - it's been set as low as 60 but atm it's on 120 - it's not just azerues either - it's also happening with KTorrent on kUbuntu(linux) - comes up as Stalled whenever i use a browser at the same time as it's downloading, comes correct again after maybe 4-5 minutes of not using the browser - what i have noticed in the NAT translations view is that the default nat rule 4294967295 is doing the forwarding
(see here - "23 4294967295 ppp-0 TCP - Outside 1796")
and not the NAT rule i set up for BitTorrent - could this be an exploit of some kind??? using the bittorrent protocol to attempt some kind of intrusion as thats a explanation that works as it's only recently started happening, what if that intrusion attempt was on port 80 and using the stateful entry gained from BT to try to pry open a otherwise protected port would that cause this?!, what if i delete the default rule to force it only to forward my BT port? can i do this?
Java, that is the "napt" rule, witch is for outgoing connexions. There should be other entries for the BT Port-forward (you may want to enable logging on that rule so that you can better watch its activity).
Reading you description, not much comes to mind; two things; first, perhaps something nefarious, so disconnect your DSL, wait ten minutes. Change the port you use for BT to something very different, reconnect DSL and see how things are (with different torrents, if possible, and disable any other servers you have running, for now). If the problem returns say ten to thirty minutes later, investigations along these lines can continue.
And the second; perhaps it's the browser. You haven't tweaked its pipelining capabities, have you? (by the way, this practice is not recommended)
;o)
I'm having a similar problem to Java.
Running http and Torrants at the same time just dosen't work, even email from outlook gets stuck, and the torrant will slow down to a crawl in both directions. I'm setting the maximum upload as low as 10kbs with no change.
Pausing or canceling the download frees things up again, but after a particually long session the net remains 'twichy' for some time. If http stops completely, it'll be about five minutes before it works again.
I'll try swaping the ports to see if that changes anything.
Your answer is probably up there
;o)
Posting here is disabled at this time.